This is a group project of SDSC4116 – Data Science Capstone. I did the project in my final year 2023/24 Semester B.
Presentation Slides:
Supervisor: Prof. CHEN Minghua
Abstract
A Crypto wallet is a Digital and Decentralized system where users may securely authenticate themselves across both Web2 and Web3 services using their Private Keys. The Ecosystem is specifically built to accommodate private keys that are safeguarded using cold or hardware wallets, which produce and secure private keys offline. Users have the option to isolate their private keys from the internet when they are not being used, so safeguarding them from continuous vulnerability to hackers. Cold wallets guarantee that the user generates the private key from the start and does not keep it on any centralized servers.
The Decentralised Ecosystem will offer users a fundamental framework for managing and utilizing their private keys in both Web2 and Web3 applications, enabling them to remain connected while preserving their digital autonomy. By integrating the wallet with many services in the decentralized ecosystem, customers may maintain control over their money and data, even if they lack expertise in advanced cybersecurity.
1. Background
During the early days of Web 1.0, the internet was limited to delivering information to users in a one-way fashion, similar to basic website browsing. This was referred to as the “read-only” web. In the era of Web 2.0, driven by influential tech companies, there was a notable shift towards interactive social networks like Facebook, Twitter, and Blogs. These platforms were often referred to as the “read-write” web because of their highly interactive features.
A New version of the Internet, known as the World-Wide-Web, is currently being developed. Web3, sometimes referred to as Web 3.0, encompasses the principles of Decentralization, Cryptocurrencies, Blockchain technology, and Token-based economy.

1.1 Why do we adopt Web3.0 instead of Web2.0?
Web3 empowers individuals to exercise control over their Digital Security and Privacy by using the Private key, which serves as exclusive cryptographic evidence of the user’s identity and data on the internet. With each user having responsibility for their own security, the decentralized structure of Web3 offers a higher level of security compared to Web2. Web 3.0 encrypts data fully, making it impossible for any government or entity to shut down websites and services. It is impossible for any one person to manipulate someone else’s identity. Users will have full control over their data and enjoy enhanced security measures, allowing them to share information according to their preferences.
Additionally, Web 3.0 has made other significant contributions. Cryptocurrencies and their associated blockchains have revolutionized transactions, making them faster and more convenient than ever before. This enables faster completion of transactions such as lending, asset investments, and payments, thereby promoting the growth of cross-border economic activities.
1.2 What is Decentralised Security?

Decentralization with Blockchain Technology: Transparency, Immutability
Data on the Blockchain is public, and visible to everyone. Ledgers are distributed among all participants, and every change requires consensus from the majority. Continuous encryption and verification ensure security, with all details openly displayed. Compared to centralized structures, such as data stored in bank databases, decentralization greatly enhances transparency, significantly reducing the possibility of opaque practices. Because every update requires verification and consensus, unilateral alterations are not feasible. Once transactions are packaged and encrypted, they are immutable once on the chain, a characteristic of Blockchain known as “Immutability” .
Decentralized security refers to a system of security where the responsibility and control over security measures are distributed over multiple nodes or entities rather than being centralized in a single authority. This approach to digital security is contemporary, allowing users to have control over the protection and confidentiality of their assets and data through the use of a private key. Decentralized security is a more secure alternative to centralized security, as it eliminates the need for a single administrator to protect many digital identities from cyber threats.
1.3 What is a Private Key?
A Private key is a cryptographic code that is used to encrypt and decrypt data in a secure manner. It is verified through a distinct sequence of characters that functions as cryptographic evidence. A private key has the ability to decrypt encrypted data and grant permission or authorization for the content of the encrypted data. In order to maintain control over their digital identity, assets, and data, it is imperative for the holder to safeguard the confidentiality of their private key, as any failure to do so may result in loss of control.
1.4. Problems of Web2
1.4.1 Data leaks
Data breaches targeting companies that protect sensitive personal data occurred 3,205 times in 2023. Hackers, including possible insiders, can target a centralized server with one attack instead of several across a network. Hackers are deterred from targeting decentralized security systems because it takes time and is wasteful.
1.4.2 Privacy of Information Breach
Web2 firms trade personal data for services. Thus, most digital users willingly supply personal information like names, birthdates, and addresses to use web services like e-commerce and social media. Large technology businesses are also known for tracking users’ internet activity and profiting from their data.
1.4.3 Asset Ownership Loss
Most asset owners trust exchanges and banks to manage their holdings. Many fail to comprehend that such action relinquishes authority. Asset managers can restrict withdrawals indefinitely during a bankruptcy, bank run, or war.
1.5 Solution: Crypto Wallets in Web3
A Crypto wallet allows users to securely store, manage, and transact with their cryptocurrencies and other blockchain-based assets. As data science students, we prioritize comprehending and executing data privacy and security procedures. We explore the complexities of protecting confidential information and ensuring that data management processes comply with legal and ethical guidelines. To choose the perfect crypto wallet, we set up Three Essential Elements that a crypto wallet should have: Robust Security features, Enriching User Experience, and Functional Features.
1.5.1 Robust Security Features
It is essential to prioritize Reputation and Credibility when selecting a wallet service. Seek out platforms with a proven history of robust security measures and receive favorable customer feedback to help inform your decision. In addition, it is crucial to evaluate the security features provided by the wallet carefully. This includes considering factors such as multi-signature authentication and PIN protection, which can help create a secure environment for your transactions. Take into account whether the wallet is open-source or closed-source, carefully considering transparency and trust as important factors in your decision-making process.
1.5.2 Enriching User Experience
To improve our crypto wallet’s user experience, we prioritize Simplicity, an Intuitive User Interface, and Accessibility. Our mobile app offers a seamless user experience, making critical functionality accessible even when on the go. Users receive detailed tutorials for product setup and use. Users can also get help from our devoted customer support team. We prioritize ease of use, instructional information, and fast support to empower users to confidently and easily manage cryptocurrencies.
1.5.3 Functional Features
When selecting a cryptocurrency wallet, it is crucial to prioritize Adaptability and Uses. A multi-cryptocurrency wallet enables the creation of diverse investment portfolios. Connecting with exchanges streamlines the process of trading, while engaging in staking and yield farming generates passive income. Multi-signature functionality enhances the security of users who prioritize safety, while the inclusion of NFT support caters to the needs of individuals who gather digital assets.
Summary of a Perfect Wallet
Feature Category | Description | Examples |
|---|---|---|
Robust Security Features | -Encryption: Protects sensitive information with complex algorithms. -Multi-factor authentication (MFA): Requires multiple forms of verification. | -Trezor -Ledger -MetaMask |
User Experience | -Ease of use: Simple designs and smooth experiences -Integrated tutorials: Help users get started -Responsive customer support: Assists Users in need | -Coinbase -Binance Academy |
Functional Features | -Multiple Cryptocurrencies: Supports a wide range of digital assets -Integration with exchanges: Allows for seamless trading -Advanced features: Supports dApps staking, and yield farming | -Binance -Atomic Wallet -MetaMask -Trust Wallet |
2. Introduction of Crypto Wallet
A Crypto Wallet allows users to securely store, manage, and transact their cryptocurrencies and interact with blockchain networks. It consists of a public address, which serves as an identifier for receiving funds, and a private key, which acts as a password for accessing and controlling the assets stored in the wallet. Crypto wallets come in various forms, such as hardware wallets (physical devices), software wallets (desktop or mobile applications), and web-based wallets (accessible through online platforms). They provide an essential interface for users to interact with decentralized networks, enabling them to send and receive cryptocurrencies, view transaction history, and connect to decentralized applications (dApps) within the Web3 ecosystem.
2.1 Wallet Programs
Wallet programs create public keys to receive satoshis and use the corresponding private keys to spend those satoshis. Permitting the receiving and spending of satoshis is the only essential feature of wallet software—but a particular wallet program doesn’t need to do both things. Two wallet programs can work together, one program distributing public keys to receive satoshis and another signing transactions spending satoshis.
Wallet programs must also interact with the peer-to-peer network to get information from the blockchain and broadcast new transactions. However, the programs that distribute public keys or sign transactions don’t need to interact with the peer-to-peer network themselves.
This leaves three necessary but separable parts of a wallet system: a public critical distribution program, a signing program, and a networked program. Since most of the wallets combine all three functions, the Full-service Wallets will be discussed mainly.
The most straightforward wallet is a program that performs all three functions:
it generates private keys, derives the corresponding public keys, helps distribute those public keys as necessary, monitors for outputs spent to those public keys, creates and signs transactions spending those outputs, and broadcasts the signed transactions.
The main advantage of full-service wallets is that they are easy to use. A single program does everything the user needs to receive and spend satoshis.
The main disadvantage of full-service wallets is that they store the private keys on a device connected to the Internet. The compromise of such devices is common, and an Internet connection makes it easy to transmit private keys from a compromised device to an attacker.
2.2 Types of Crypto Wallets:
Cryptocurrency wallets come in various forms, each with its unique features and security levels. The three primary categories of crypto wallets are hardware, software, and paper wallets. These wallets can be further classified as either cold or hot wallets, depending on their connectivity to the internet.
Software wallets, also known as hot wallets, are digital wallets that are easily accessible through mobile devices or computers. They offer convenience and flexibility, allowing users to manage their cryptocurrencies quickly. However, their constant internet connectivity makes them more vulnerable to potential hacking attempts and security breaches.
Among the various types of crypto wallets, hardware wallets like Ledger and Trezor stand out for their robust security features. Designed for the long-term storage of cryptocurrencies, these devices keep private keys offline, safeguarding them against online hacking attempts.
2.3 Misconceptions About Crypto Wallets
A popular misconception about crypto wallets is that they contain or actually store actual crypto. However, that is not the truth.
Taking Bitcoin as an example, to better understand how Bitcoin wallets operate without actually storing bitcoins, it is helpful to draw comparisons to traditional financial systems and explore the concept of Unspent Transaction Outputs (UTXOs).
In the traditional banking system, a credit card serves as a tool for accessing and managing funds stored in a bank account. The credit card itself does not store any money; instead, it provides a means to authorize transactions and transfer funds between accounts. Similarly, a Bitcoin wallet does not store bitcoins but manages the private and public keys that grant access to the user’s Bitcoin addresses recorded on the blockchain.
Bitcoin transactions rely on the concept of UTXOs, which represent the available balance of bitcoins that can be spent. When a user receives bitcoins, the transaction creates a new UTXO, which is assigned to their Bitcoin address. The user’s wallet keeps track of these UTXOs associated with their addresses.
Imagine the blockchain as a ledger, recording every transaction. When you receive bitcoins, it’s like getting a voucher (UTXO) that says how much you have. Your wallet keeps track of these vouchers. When you send bitcoins, your wallet uses these vouchers, signs them with a digital ‘signature’ to prove they’re yours, and then sends them on. It’s a bit like endorsing a check to someone else.
In conclusion, Bitcoin wallets do not store bitcoins directly, just as credit cards do not store money. Instead, wallets manage the private and public keys that grant access to UTXOs recorded on the blockchain. By utilizing these keys, users can control their funds and authorize transactions without the need for the wallet to store the bitcoins themselves.
2.4 Transaction Process
Transaction is the primary function of a crypto wallet to interact with the blockchain. A good wallet should support the transaction in most blockchain networks. Taking the Bitcoin network as an example, Bitcoin transactions could facilitate the transfer of value between users. Understanding the technical aspects of the transaction process is crucial for developers, researchers, and users seeking to leverage the benefits of this decentralized system. The transaction process usually includes the following steps:
1. Transaction Initiation
A Bitcoin transaction begins when the sender opens their Bitcoin wallet and enters the recipient’s Bitcoin address and the amount of BTC to be sent. The wallet creates a simple transaction note that says where the bitcoins are coming from, who they’re going to, and how much is being sent. It also includes a secure digital signature to prove that the sender has the right to send the bitcoins.
2. Digital Signature
To prove ownership and authorize the transaction, the sender’s wallet uses its private key to create a digital signature. The digital signature works like a handwritten signature on a check, proving that you agree to the transaction and that it’s really you who’s sending the money.
3. Broadcasting the Transaction
Once the transaction is signed, the wallet broadcasts it to the Bitcoin network. The transaction message propagates across a network of Bitcoin nodes, which are computers running the Bitcoin software. This decentralized broadcasting ensures that the transaction reaches a wide range of nodes for validation.
4. Transaction Verification
Network nodes verify its validity upon receiving the transaction by checking its adherence to the consensus rules. This includes ensuring that the transaction does not involve double-spending and that the digital signature is correct. Valid transactions are then added to a pool of unconfirmed transactions known as the mempool.
5. Mempool and Transaction Fees
Transactions in the mempool await inclusion in a block by miners. To prioritize their transactions, senders can attach higher transaction fees, incentivizing miners to include them in the next block they create.
6. Mining and Block Inclusion
Think of miners as specialized accountants who gather several transactions, check them, and then group them into a single ‘page’ of the Bitcoin ‘ledger’. They engage in a competitive process called mining, attempting to solve a complex mathematical puzzle (proof-of-work) to validate the block. The first miner to solve the puzzle appends the block to the blockchain and receives a block reward and transaction fees.
7. Transaction Confirmation
Once a transaction is included in a block, its first confirmation is obtained. Subsequent blocks added to the blockchain provide additional confirmations, strengthening the transaction’s security. Typically, six confirmations are considered sufficient for most transactions to be deemed secure.
8. Updating the Blockchain
The newly added block containing the transaction is propagated across the network, and all nodes update their local copy of the blockchain to reflect the changes. This ensures that the blockchain remains consistent and immutable across the entire network.
9. Recipient Receives the Funds
The recipient’s wallet continuously monitors the blockchain for incoming transactions. Once the transaction is detected, the received BTC is added to the recipient’s wallet balance, making it available for future transactions.
In summary, sending bitcoins is a secure process that goes through several checks and balances. It’s like sending a digital package that gets sealed and delivered with care, ensuring that only the right person can open it. This process is part of what makes Bitcoin a trusted and transparent way to transfer value.
3. Comparative Analysis of HashNut with Mainstream Wallets
In our exploration of the current world of crypto wallets, including HashNut, Coinbase, MetaMask, Binance, TrustWallet, OKX, Bybit, and Bitget, we conducted a series of tests focused on evaluating each wallet’s adherence to the essential features of a good crypto wallet. This evaluation centered around three main parts: security features, user experience, and functional features.
3.1 Security Features Comparison
3.1.1 Encryption & Authentication:
Coinbase:
- Coinbase employs strong encryption techniques to secure user data and funds. It also supports two-factor authentication (2FA) through various methods, including Google Authenticator, Duo, and SMS codes. This dual-layer security ensures that even if a password is compromised, unauthorized access is still preventable.

[Coinbase 2FA setup interface]
Binance:
- Similar to Coinbase, Binance emphasizes user security by implementing robust encryption standards. For 2FA, Binance allows users to enable Google Authenticator or SMS authentication. Binance also introduces device management, which provides an extra layer of security by allowing users to manage and review devices that can access their accounts.

[Binance device management dashboard]
MetaMask:
- While MetaMask primarily focuses on the encryption of private keys and data locally on the user’s device, it also encourages the use of hardware wallets for an added layer of security. This approach ensures that the private keys are not just encrypted but are also kept offline, reducing the risk of online theft.

[MetaMask hardware wallet integration]
HashNut:
- Upon reviewing HashNut’s security measures, it’s noted that HashNut has not publicly disclosed the specific encryption or authentication algorithms it employs. This lack of transparency could potentially raise concerns among users regarding the robustness and reliability of HashNut’s security infrastructure. In the digital asset space, where the security of user data and funds is paramount, adopting and clearly communicating strong security measures is essential.
- It is suggested that advanced encryption methods be implemented to align with industry standards and increase user confidence. Utilizing industry-standard encryption algorithms, such as AES (Advanced Encryption Standard) for data at rest and TLS (Transport Layer Security) for data in transit, would significantly enhance the security of user data and funds. Publicly disclosing the adoption of such encryption standards can also reassure users about the safety of their assets.
3.1.2 Private Key Management:
Trust Wallet:
- Backup Facilities: Trust Wallet offers a straightforward process for backing up wallets. During the initial setup, it provides users with a recovery phrase, ensuring that users can recover their funds in case of device loss.
- Importing and Exporting Keys: Trust Wallet simplifies the process of importing and exporting private keys. This feature is particularly useful for users who wish to migrate from one wallet to another or for those who prefer to manage their keys manually.
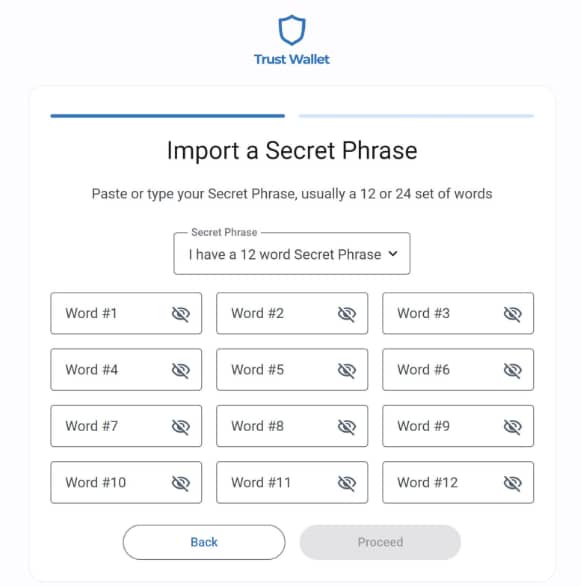
[Trust Wallet recovery phrase setup]
MetaMask:
- Private Key & Seed Phrase Management: MetaMask emphasizes the importance of the seed phrase, which is a critical component for wallet recovery. It provides clear instructions on how to secure the seed phrase and the risks of losing it. MetaMask also allows users to directly view and export their private keys, giving them complete control over their assets.
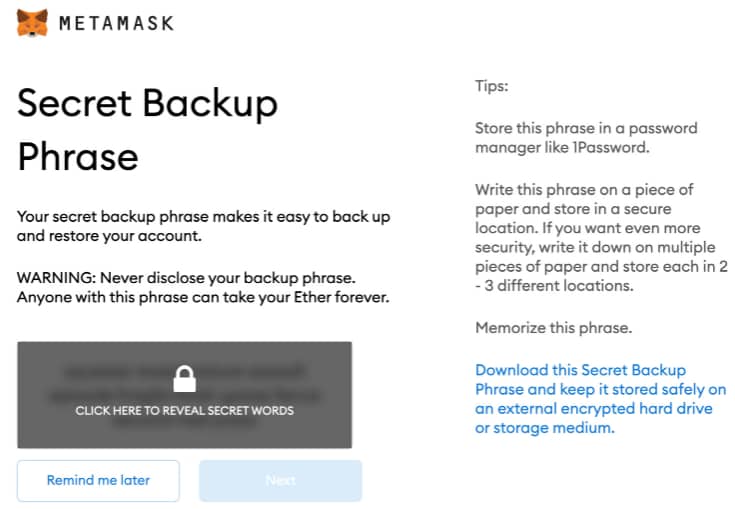
[MetaMask seed phrase management screen]
HashNut:
- HashNut provides basic private key management but lacks the comprehensive backup and recovery options found in other wallets. HashNut should introduce a more robust backup system, including a recovery phrase, and enhance the ability to import and export keys. This would improve the overall user experience and security.
3.1.3 Hardware Wallet Integration:
Ledger & Trezor with MetaMask:
- MetaMask supports integration with hardware wallets like Ledger and Trezor. This integration combines the convenience of MetaMask’s interface with the security of hardware wallets. Users can sign transactions and interact with decentralized applications without exposing their private keys to the internet. But HashNut is missing this feature.

[MetaMask connected to Ledger hardware wallets]
HashNut:
- Currently, HashNut does not offer integration with hardware wallets. Integrating this feature would provide an additional layer of security for HashNut users, allowing them to keep their private keys offline and reduce the risk of online attacks.
3.1.4 Enhanced Security Practices:
Coinbase:
- Fighting Phishing Attacks: Phishing attacks are when scammers try to trick you into giving them your personal information, like your password or credit card number. They often do this by pretending to be a trustworthy entity in an email or on a website. Coinbase provides helpful guides and tips to teach you how to spot these phishing scams. They want to make sure you know what a phishing attempt looks like so you can avoid falling for one.
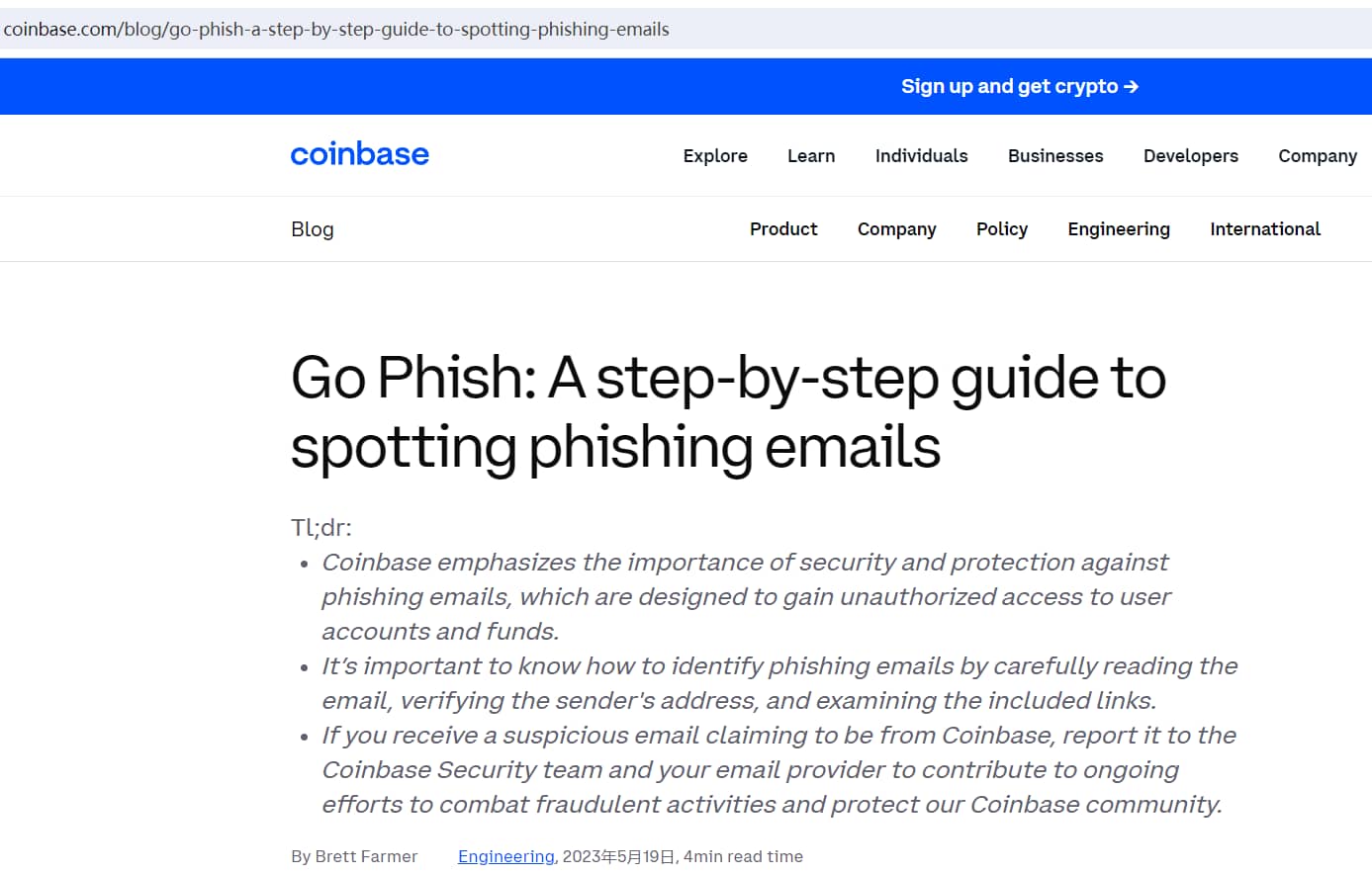 [Coinbase phishing awareness tips]
[Coinbase phishing awareness tips]
- Session Control: Binance offers features like session timeouts and device management to automatically log users out from inactive sessions or unauthorized devices, adding another layer of security against unauthorized access.

[Binance session timed out warning]
HashNut:
- HashNut should consider adopting similar enhanced security practices, such as implementing phishing protection measures and session control. These additions would help protect users from common security threats and improve the overall safety of the platform.
In conclusion, while HashNut provides basic security features such as it is a decentralized wallet, there is room for improvement in areas such as encryption and authentication, private key management, hardware wallet integration, and enhanced security practices. By addressing these gaps, HashNut can elevate its security standards and provide a safer and more trustworthy experience for its users.
Feature | Coinbase | Binance | MetaMask | Trust Wallet | HashNut (Proposed Improvements) |
|---|---|---|---|---|---|
Encryption & Authentication | – Strong encryption techniques – Supports 2FA (Google Authenticator, Duo, SMS) | – Robust encryption standards – Supports 2FA (Google Authenticator, SMS) – Device management | – Encryption of private keys and data – Encourages use of hardware wallets for added security | – Encrypted Cloud Backups | – Implement stronger encryption methods – Introduce two-factor authentication options |
Private Key Management | – Emphasizes seed phrase management – Allows export of full private keys and backup of MPC Wallets | N/A (Binance is a centralized wallet.) | – Emphasizes seed phrase management – Allows direct view and export of private keys | – Straightforward backup process – Simplifies importing and exporting keys – Provides users with a recovery phrase | – Introduce a robust backup system with a recovery phrase – Enhance the ability to import and export keys |
Hardware Wallet Integration | – Supports Ledger hardware wallets | – Supports Ledger and Trezor | – Supports Ledger and Trezor | – Supports Ledger hardware wallets | – Integrate with hardware wallets like Ledger and Trezor |
Enhanced Security Practices | – Phishing protection | – Phishing protection – Educational resources – Session control (timeouts, device management) | – Security Snaps – Privacy-Preserving Security Alerts | – Built-in Security Scanner | – Implement phishing protection measures – Adopt session control features |
3.2 User Experience Comparison
Our testing highlighted several user experience issues in HashNut compared to other mainstream wallets:
3.2.1 Interface Design:
- MetaMask’s interface is praised for its intuitiveness and easy navigation. It features a standout network management system that allows users to switch networks easily and integrates a search function for quick access. In contrast, HashNut’s interface presents an overwhelming list without search capabilities. HashNut should enhance its interface design to include a similar network management system, making it easier for users to navigate and find the networks they need.
![[Switching network in MetaMask]](https://mlcznkdztmb6.i.optimole.com/w:auto/h:auto/q:mauto/ig:avif/f:best/https://philip.twinight.co/portfolio/wp-content/uploads/2024/11/switching-network-in-metamask.jpeg)
[Switching network in MetaMask]
- Binance’s wallet interface excels in organizing a vast array of features coherently, ensuring that both new and experienced users can navigate through its services efficiently. It contrasts with HashNut’s more cumbersome interface, lacking quick access buttons and a well-structured menu system. HashNut should adopt a more user-friendly interface design, incorporating quick access buttons and a more precise menu system to improve user experience.

[Binance wallet interface with quick access buttons]
3.2.2 Ease of Use:
- OKX stands out for preventing users from adding duplicate networks or tokens, a common issue in HashNut, thereby streamlining the asset management process. To address this, HashNut could implement a feature to prevent duplicate entries, simplifying asset management and enhancing user experience.


[OKX wallet showing no duplicate network addition] vs [HashNut allows adding duplicate network]
- Trust Wallet provides clear and concise instructions for each action within the wallet, including a straightforward process for adding custom tokens and managing private keys. HashNut could improve its ease of use by offering more detailed instructions and guidance to guide users through complex processes, making the overall experience more user-friendly.


[Adding custom tokens in Trust Wallet]
3.2.3 Accessibility:
- Trust Wallet’s “Receive” UI is intuitive and easy to understand, clearly indicating how to switch networks. In comparison, HashNut’s “Receive” UI is confusing for users as they must pre-add the network first. However, it could be complicated for users to find the correspondent network they want since there is not a searching function. HashNut should adopt a more direct and clear approach in its UI design by simply adding a search function on the network list.

[Trust Wallet’s concise “Receive” UI]

[Trust Wallet allows Search directly to find the network]
- Coinbase Wallet focuses on making the cryptocurrency experience accessible to a mainstream audience, with a simple interface and rich guidance. HashNut could enhance its accessibility by simplifying its interface and providing more guidance, such as small tips to help users with minimal crypto knowledge understand the features and processes involved.

[Coinbase Wallet’s simple interface with educational content]
In conclusion, HashNut could significantly improve its user experience by adopting features and design elements from mainstream wallets such as MetaMask, Binance, OKX Wallet, Trust Wallet, and Coinbase Wallet. By addressing issues related to interface design, ease of use, and accessibility, HashNut could be more competitive and appealing to a broader range of users.
Feature | MetaMask | Binance | OKX Wallet | Trust Wallet | HashNut (Proposed Improvements) |
|---|---|---|---|---|---|
Interface Design | – Intuitive navigation – Network management system with search | – Coherent organization of features – Quick access buttons | – Prevents adding duplicate networks/tokens | – Clear instructions for actions | – Enhance interface design with network management system with search function – Adopt a more user-friendly interface with quick access buttons |
Ease of Use | – Easy network switching | – Efficient navigation for new and experienced users | – Streamlines asset management process | – Straightforward process for adding custom tokens and managing private keys | – Implement feature to prevent duplicate entries – Offer detailed instructions and educational content |
Accessibility | – User-friendly interactions | – Well-structured menu system | – Simplifies asset management | – Intuitive “Receive” UI – Educational content | – Adopt a clear and direct “Receive” UI – Simplify interface and provide educational content |
3.3 Features Comparison
Our analysis revealed several gaps in HashNut’s features compared to other mainstream wallets:
3.3.1 Support for Multiple Cryptocurrencies:
- Binance Wallet: Binance supports an extensive range of cryptocurrencies, offering users the ability to manage a diverse portfolio from a single wallet. Its support extends beyond the major cryptocurrencies to include lesser-known altcoins and tokens.


[Binance Wallet showing a wide range of supported cryptocurrencies]
- HashNut: Currently, HashNut’s support for multiple cryptocurrencies is limited. It is proposed that HashNut should expand its support to include a wider range of cryptocurrencies, including altcoins and emerging tokens. This would provide users with a more versatile platform to manage their investments and explore different blockchain ecosystems.

[HashNut does not support USDT Bep20]
- Bybit Wallet: Bybit offers substantial support for various cryptocurrencies, making it a special choice for users interested in both popular and emerging digital assets.
- HashNut: To compete with Bybit, HashNut should continually update its asset support to include the latest tokens and coins in the market. This adaptability would make HashNut an attractive option for users keen on keeping pace with the rapidly evolving cryptocurrency landscape.
3.3.2 Integration with Exchanges:
- OKX Wallet: OKX distinguishes itself with its deep integration with the OKX exchange, providing a seamless transition between wallet storage and trading.
- HashNut: HashNut lacks this level of integration with exchanges. It is suggested that HashNut should implement deeper integration with exchanges to allow users to move their assets between their wallet and trading platforms quickly. This would enhance the trading experience by offering convenience and security.
- Bitget Wallet: Bitget offers integrated exchange functionalities, enabling users to engage in trading directly from their wallets.

[An exchange integrated with Bitget Wallet]
- HashNut: To match Bitget’s capabilities, HashNut could introduce integrated exchange functionalities, simplifying the trading process and enabling users to take advantage of market movements quickly.
3.3.3 Custom Assets:
- Trust Wallet: Trust Wallet provides an intuitive approach to managing custom assets, allowing users to add new tokens and keep their wallet organized easily.
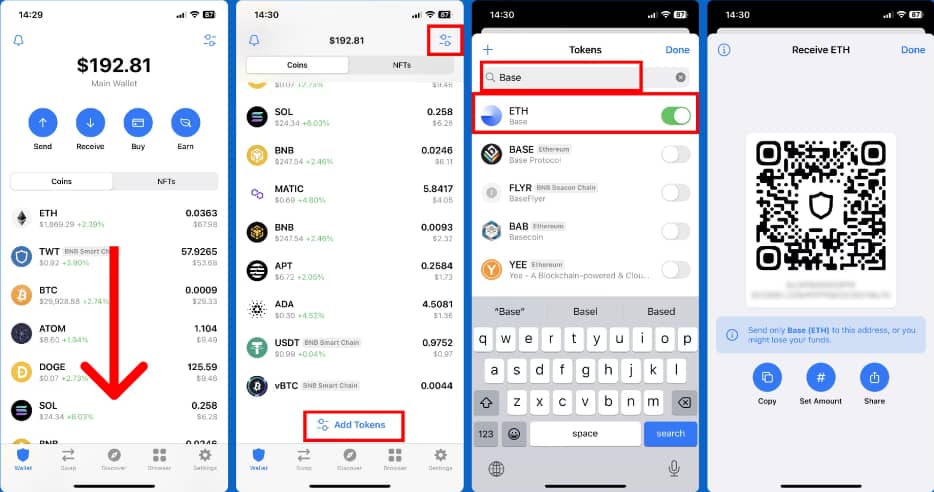
[Fewer steps in adding new token in Trust Wallet] - HashNut: HashNut’s management of custom assets is not user-friendly enough. For example, after users have added a new asset in HashNut, they are not able to delete it.HashNut should enhance its custom asset management by allowing users to add, remove, and edit tokens easily. This would provide users with greater flexibility and control over their portfolios.






[Hashnut’s interface for managing custom assets, without delete asset after added it]
- MetaMask: MetaMask allows users to add custom tokens to their wallet using the token’s contract address, making managing a wide array of assets easy.


[Adding custom token on MetaMask]
- HashNut: To improve its user experience, HashNut could implement a similar feature, enabling users to add custom tokens and manage them effectively. This is crucial for users who participate in DeFi projects or hold tokens that are not widely recognized.
In conclusion, HashNut could significantly improve its user experience by enhancing its support for multiple cryptocurrencies, integrating more closely with exchanges, and providing more sophisticated custom asset management. These improvements would align HashNut more closely with the standards set by leading wallets in the industry and make it a more attractive option for a diverse user base.
Feature | Binance Wallet | OKX Wallet | Trust Wallet | MetaMask | HashNut (Proposed Improvements) |
|---|---|---|---|---|---|
Support for Multiple Cryptocurrencies | – Extensive range of cryptocurrencies – Includes altcoins and tokens | – Integrated with OKX exchange | – Intuitive approach to managing custom assets | – Allows adding custom tokens using contract address | – Expand support to include a wider range of cryptocurrencies – Continually update asset support for the latest tokens and coins |
Integration with Exchanges | – Binance Connect, formerly known as Bifinity | – Deep integration with OKX exchange – Seamless transition between wallet and trading | – Supports connection between user’s Trust Wallet account and accounts on supported centralized exchanges | – Supports interaction with various blockchain applications and networks | – Implement deeper integration with exchanges – Allow easy movement of assets between wallet and trading platforms |
Custom Assets | N/A | – Supports adding custom ERC-20 or other network tokens with the address | – Easy addition of new tokens – Simplified process for removing or editing custom assets | – Easy management of a wide array of ERC-20 tokens and other Ethereum-compatible standards | – Enhance custom asset management – Allow easy addition, removal, and editing of tokens |
3.4 Gap Analysis Using Our Test Cases:
In reviewing feedback and testing HashNut, it’s clear that HashNut has some shortcomings compared to its competitors. One main issue is its search function within the wallet interface, which makes it hard for users to find specific features or assets. The transaction history provided by HashNut is also lacking in clarity and functionality, making it tough for users to keep track of their activities. Additionally, the process of adding and managing contacts could be improved, as well as the features related to QR code payments, where competitors seem to do better. HashNut’s overall interface is also seen as less user-friendly than its rivals.
From a security perspective, the lack of two-factor authentication in HashNut is a major weakness, along with concerns about how it handles private keys. This is in stark contrast to the stronger security measures found in competing wallets. Regarding user interface and functionality, HashNut users have reported difficulties with managing assets and switching networks, whereas competitors offer more seamless and intuitive solutions. Moreover, HashNut is missing advanced features like real-time updates on gas fees and the ability to specify amounts in QR code payments, which are available in other wallets.
These gaps highlight the need for HashNut to make significant improvements in several areas. Adding two-factor authentication, making the user interface more engaging and intuitive, and expanding its features to include things like live gas fee updates and better QR code transactions are key steps. Addressing these issues based on user feedback and test case analyses is crucial for improving HashNut’s market position and meeting mainstream cryptocurrency wallets’ standards.
4. Impact Conclusion and Additional Contributions
During the course of the project, our team has successfully identified and documented 46 suggestions encompassing various aspects, including user interface (UI), bug fixes, feature enhancements, and workflow optimizations. Based on extensive discussions with the development team, each suggestion has been meticulously evaluated and classified with a priority level of High, Medium, or Low. These priority levels reflect the urgency and potential impact of each suggestion on the product’s overall user experience and functionality.
In addition to providing comprehensive suggestions, we have gone the extra mile to offer practical and feasible solutions for improvement. Our recommendations take into account multiple factors, such as the associated development costs, technical complexities, and the competitive landscape of the market.
Our approach demonstrates a commitment to delivering actionable insights that strike a balance between innovation and pragmatism. By presenting both impactful and realistic suggestions, we hope to maximize the value of the project and position the product for success in an increasingly competitive market.
4.1 Impact of recommendations
- Add Network Enhancement: HashNut has implemented a search bar and filter options to make it easier for users to find networks within a long list. Users can now search by network name or chain ID, and a fast scroll bar with an alphabetical index has been added for quicker navigation. The network list can also be ordered by the alphabet or chain ID, with the chain ID displayed in the user interface for clarity.
- Custom Asset Bug Fix: The issue of existing tokens being repeatedly added to the “Custom Asset” page has been addressed. HashNut has fixed this by implementing a warning system or removing the option to add a network that has already been added, preventing duplicate entries.
- Wallet Setting Bug Fix: The problem with importing wallets from OKX using a private key, where the ‘continue’ button was not available, has been resolved. This ensures that users can now seamlessly import their wallets using private keys without encountering interface issues.
These enhancements and bug fixes demonstrate a clear impact on the usability and functionality of the HashNut wallet, reflecting the successful adoption of the recommendations provided. The detailed list of adopted suggestions and the acknowledgment letter from the CEO, Edward, will serve as formal documentation of these improvements.
4.2 Additional Contributions Beyond Wallet Improvement Recommendations
In addition to suggesting ways to improve the HashNut wallet, our team also talked about the future of the platform. We discussed how crypto wallets might change and how more people could start using cryptocurrencies in their daily lives. These talks were meant to give HashNut valuable ideas for long-term growth and success.
Besides the product research, we also helped build a community around HashNut’s inscription feature on Reddit. This project aims to create an active and engaged community around this exciting feature, which has a lot of potential for attracting and keeping users.
Moreover, we actively took part in the Asian Financial Forum (AFF) to promote HashNut and look for potential clients. At the event, we met many talented people who are passionate about Web3 projects. These interactions let us showcase what HashNut can do, get useful feedback, and explore possible partnerships and collaborations that could help the platform grow and succeed.
Our team’s work went beyond just giving advice on how to improve the HashNut wallet. By having forward-thinking discussions, creating a dedicated inscription community, and actively promoting HashNut at the AFF, we aimed to contribute to the platform’s long-term development and success in the fast-changing world of cryptocurrencies and Web3 technologies.
Throughout our final year project, I took on several important roles in analyzing and improving crypto wallets. In Part 1, I worked on creating a simple and informative introduction to blockchain and cryptocurrencies for people who are new to the concept as well as those who already know a lot about it. This involved doing a lot of research and testing different Web3 wallets to figure out what makes a good one and how we can make HashNut even better. In Part 2, I helped research how blockchains keep our assets safe. In Part 3, I focused on testing HashNut’s app, finding and analyzing problems with it, and giving suggestions to the development team on how to fix them. I also suggested that HashNut should create a community in the crypto world and run projects where users can get free tokens to encourage more people to join. Overall, I learned that developing Web3 technology isn’t easy, but it’s definitely possible with teamwork and good ideas.
Reference
Abdullah, A., & Nor, R.B. (2018). A Framework for the Development of a National Crypto-Currency. International Journal of Economics and Finance.
Antonopoulos, A. M. (2017). Mastering Bitcoin: Programming the Open Blockchain (2nd ed.). O’Reilly Media.
Bharany, S., & Maashi, M.S. (2023). A Critical Investigation into the Blockchain Technology and Its Present-Day Uses. 2023 3rd International Conference on Computing and Information Technology (ICCIT), 69-72.
Buterin, V. (2014). A next-generation smart contract and decentralized application platform. https://ethereum.org/en/whitepaper/
Cyril, U.M., Nwadiuto, E.P., & Francisca, A.N. (2024). Crypto Currency on the Development of Nigeria Banking System with Particular Reference to the First Bank Nigeria Plc. IIARD INTERNATIONAL JOURNAL OF BANKING AND FINANCE RESEARCH.
Kaloev, M., & Krastev, G. (2023). A Practical Guide to Deploying Smart Contracts and Orchestrating Digital Ecosystems: Transitioning from Fiat Payment Systems to Digital Economies for Institutional and Academic Institutions. 2023 31st National Conference with International Participation (TELECOM), 1-4.
Kanegae, L.C., Cernev, A., & Diniz, E.H. (2021). Moeda Seeds: E-Commerce and Crypto Solutions for Development.
Kumar, A. (2021). A Study of the Impact of Crypto Currency on the Indian Payment system. Asian Journal of Management.
Mirza, M.M., Ozer, A., & Karabiyik, U. (2022). Mobile Cyber Forensic Investigations of Web3 Wallets on Android and iOS. Applied Sciences.
Nakamoto, S. (2008). Bitcoin: A peer-to-peer electronic cash system. https://bitcoin.org/bitcoin.pdf
Rani, M. (2023). Digital Payment System Development in India. ANUSANDHAN – NDIM’s Journal of Business and Management Research.
Rani, P., Sachan, R.K., & Kukreja, S. (2023). Academic Payment Tokenization: An Online Payment System for Academia Utilizing Non-Fungible Tokens and Permissionless Blockchain. Procedia Computer Science.
Tapscott, D., & Tapscott, A. (2016). Blockchain Revolution: How the Technology Behind Bitcoin is Changing Money, Business, and the World. Penguin.
Wood, G. (2014). Ethereum: A secure decentralised generalised transaction ledger. Ethereum Project Yellow Paper, 151(2014), 1-32. https://ethereum.github.io/yellowpaper/paper.pdf
Yatsunami, R. (2020). Legislative Development on Crypto-Assets in Japan: Revisions to the Payment Services Act, etc.
Zheng, Z., Xie, S., Dai, H. N., Chen, X., & Wang, H. (2018). Blockchain challenges and opportunities: A survey. International Journal of Web and Grid Services, 14(4), 352-375.
